There are plenty of opportunities for content marketers to thrive in the cybersecurity industry. But as competition continues to intensify, results are harder to come by. That’s where brands might try leveraging fear-based cybersecurity content marketing.
Don’t fall into the trap of a fear-based content strategy. Here, you’ll learn why (and how) you should take an alternative approach.
The cybersecurity industry has raised an insane amount of VC money over the last few years. According to the Venture Monitor report from NVCA and PitchBook, cybersecurity funding exceeded $140 billion in 2018, $135 billion in 2019, and $69 billion in just the first half of 2020.
None of this should come as much of a surprise as global cybersecurity spending continues to increase exponentially, with analysts predicting a $133 billion market by 2022.
What does that mean for content marketers?
Two things.
First, it means there are more opportunities for you to thrive in the cybersecurity industry than ever before.
VC firms have infused tens of thousands of early- and late-stage cybersecurity companies with the money necessary to take innovation up a notch—not just on the product front but in terms of brand building, too. This is an industry where content can make a significant difference.
But the second point is that there’s more competition than ever before. Much like the martech landscape, the massive growth of cybersecurity companies has warranted a supergraphic of the market (or the CYBERscape, as Momentum Cyber calls it).

No matter what specific corner of the cybersecurity market your organization exists in, getting your content to stand out will be an uphill battle.
The push to stand out by being bolder than competitors has led to an overreliance on FUD—messaging that hits on fear, uncertainty, and doubt.
It’s a natural choice. Cyber attacks (and the costs that come with them) are dangerous for companies of all sizes. But using your content to constantly remind your audience of that isn’t the right approach.
If you want cybersecurity content marketing to work, you’ll need a more effective strategy.
The Problems with Fear-Based Cybersecurity Content Marketing
“Health Data Breach Victim Tally for 2018 Soars”.
“Judge Approves Anthem’s $115M Data Breach Settlement”.
“Hackers Are Passing Around a Megaleak of 2.2 billion records”.
These are all real headlines from cybersecurity stories. Do they grab your attention (and the attention of your target customers who are worried about attacks)? Absolutely.
One CSO explained how the cybersecurity industry has a somewhat subconscious addiction to FUD. In a CSO Online article, he wrote:
But I did notice a more negative trend with my tweets and LinkedIn posts, likes and comments. I did tend to send out multiple posts when a big data breach story broke. These posts received the most attention, likes, comments, responses and dialogue.
And it wasn’t just me. Analyzing Brian Krebs and several other well-known security bloggers, I saw even more data breach focus. I wondered if endless descriptions regarding these stories—and even breaking the news of new data breaches—hadn’t become a part of how our cyber industry survives and thrives.
He noted a few reasons why FUD is so addicting for cybersecurity pros—the viral attention, the fact that it’s easy to talk about, the focus on hard data, and more.
But the buying groups of your target prospects aren’t only made up of cybersecurity pros. And even if they were, you know that traffic doesn’t directly translate to revenue.
While FUD-based content will stand out, there’s reason to believe it’s not the best way to guide prospects from the awareness stage to a purchase decision.
4 Reasons Fear-Based Content Marketing Doesn’t Work
Fear-based messaging isn’t unique to the cybersecurity industry. Traditional advertisers and social media marketers alike have been using FUD for years to push products and services.
The Truth Initiative has been running anti-tobacco campaigns since 1998. And for a long time, their TV ads leaned heavily on fear-based messaging. They ran ads where people dropped dead inexplicably and where teens piled body bags on the yards of tobacco executives. The shift to positive messaging with the “Finish It” campaign strategy has proven more effective since 2014.
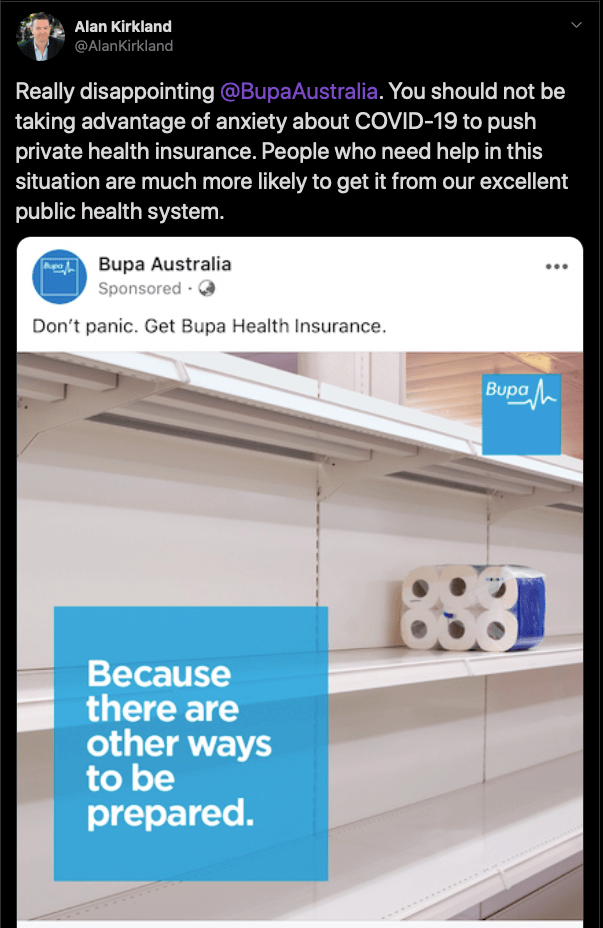
And as we live through the COVID-19 pandemic, marketers are showing just how easy it is to fall into the FUD messaging trap. One insurance provider in Australia released this tone-deaf ad in an effort to capitalize on public anxiety.
Fear-based content creates a lasting image in your head when done well. But the point is that these lasting images generally don’t translate to business results. There are four main reasons why:
- The “won’t happen to me” mindset
- The desensitization factor
- The feeling of judgment
- The long-term outcomes
FUD Problem #1: The “Won’t Happen to Me” Mindset
Cyber attacks became a pillar in mainstream media following data breaches at companies like Target (2013), Home Depot (2014), and Anthem (2015).
These are the kinds of incidents that are mentioned in cybersecurity conversations even years later. And their prevalence led to a natural message from all kinds of security brands—don’t let your company be the next Target/Home Depot/Anthem.
This kind of messaging is effective at getting business leaders to fear a data breach. However, their immediate thought isn’t to invest millions in a solution to solve the problem—it’s to manage their own fear. Instead of watching the inbound leads rack up from your content, all you’re left with is a group of target prospects with an “it’ll never happen to me” mindset.
The effect also extends to smaller businesses. As SMB leaders see headlines for data breaches at the world’s largest organizations, they’re able to distance themselves from the stories. Even though nearly half of cyber attacks target small businesses, decision-makers figure it would never happen to them.
That’s the first problem with a fear-based approach to cybersecurity content marketing. It makes business decision-makers think about cybersecurity—but doesn’t create a sense of urgency to invest in a new solution.
FUD Problem #2: The Desensitization Factor
This is an extension of the “it’ll never happen to me” situation.
You know that companies with subpar security solutions are taking a risk. But here’s the problem—it’s likely that they understand the risk, too.
The reality is that people who are willing to take risks and have that “it’ll never happen to me” mindset won’t be persuaded by negative content. They’d need to see the negative effects of a cyber attack firsthand to truly recognize that change is necessary.
As a result, your prospects start to get desensitized to fear-based content. You might have one chance to scare a particular member of the buying team into considering a cybersecurity solution. But if you don’t close the deal? Those messages will just get weaker as you rely on FUD messaging.
Your competitors are bombarding prospects with their own content marketing efforts. Don’t water down your own messaging by relying on fear.
FUD Problem #3: The Feeling of Judgment
Think about this headline: “Has an Attacker Already Compromised Your Network? You May Not Even Know It”
That’s a valid question, given how sophisticated cyber attackers have become. Countless reports have revealed that attackers can maintain footholds in a network for upwards of 100 days without being detected.
Detection technology has come a long way in recent years, but that doesn’t mean every organization is prepared. That’s where your products might come into play. But shaming a company for its cybersecurity failures may not be the best approach.
While the headline above makes the need for better security solutions clear, it’s inherently judgmental of your prospects. That’s not exactly going to get the relationship off on the right foot as you try to qualify leads.
FUD Problem #4: The Long-Term Outcomes
Let’s be honest. Cybersecurity is a necessary investment for all organizations—but that doesn’t mean it’s simple.
Whether you’re selling to a large enterprise that already has a complex IT infrastructure or a smaller business that doesn’t know much of anything about cybersecurity, the buyer’s journey is likely a long one.
That’s not news for your content marketing strategy. However, relying on fear-based content might stretch that buyer’s journey to the point that your prospects look elsewhere for a solution.
Generally speaking, people seek out instant gratification and positive short-term outcomes. Even though the cybersecurity buying process can be long, individual steps toward a purchase decision should feel positive.
When you focus on fear, you’re trying to convince customers to buy into a solution that protects them from an attack in the future (or, if they’re never targeted, no attack at all). Avoiding the long-term outlook will help create a greater sense of urgency.
Fear Is Not a Brand Differentiator
“The security bazaar is noisier and messier than ever. Every company sounds exactly like the eight others, and lines get blurred. Those that thrive will do so on differentiation.”—Ted Schlein, General Partner at Kleiner Perkins Caulfield & Byers
This quote is from a 2015 VentureBeat article about the growing intensity of competition in the cybersecurity space.
The only thing that’s changed since then? Your market has become even noisier and messier.
Product innovation is critical to the success of a cybersecurity organization. There’s no denying that. But believing a company’s IP is so strong that it could never be replicated or outpaced by competitors might be a bit naïve.
Taking the right steps to differentiate your brand will make your company stand out over the long term. And that’s where you and your content marketing program come in.
This is the ultimate downfall of a fear-based content strategy—it isn’t a brand differentiator.
Focusing your messaging on fear creates an even playing field between you and your competitors. Everyone can talk about the same exact data breach incidents and attack vectors. A FUD-based strategy will get lost in the noise.
Want your content (and your brand) to stand out? It’s time to ditch FUD and take a better approach to content.
Creating an Effective Content Strategy for Cybersecurity Brands
When you take away the safety net of FUD messaging, are you still able to create content that engages, persuades, and converts your target audience?
Of course.
But the path forward isn’t as obvious as the fear-based approach that so many cybersecurity brands default to.
To create a content strategy that will succeed in the cybersecurity industry, you’ll need:
- Clear goals and messaging that will help achieve them
- Deep insight into your buyer personas
- An understanding of the types of content that work for your industry
Let’s dig a little deeper into each point and come up with the keys to writing content that gets results for your brand.
Cybersecurity Content Marketing with a Purpose
Specific content marketing goals will vary depending on your strategy, team, and organization.
But that doesn’t mean we can’t talk about the general role of content in the cybersecurity industry.
The modern content marketing team isn’t judged by the number of leads they generate. You aren’t rewarded solely for driving more traffic to the website. And business stakeholders won’t see you as successful just because you increased the brand’s social following.
More than ever, content marketers have to show they contribute to revenue goals.
In cybersecurity, that means not just tracking lead volume but also lead quality and the role of content in driving prospects to a purchase decision.
This is why it’s so important to take an alternative approach to fear-based content marketing. Your FUD messaging might drive up those vanity metrics. But you need the real results to follow.
And that brings us to a true marketing classic—Robert Cialdini’s 6 (now 7) principles of influence. When talking about Cialdini’s book Influence: The Psychology of Persuasion, Drift CEO David Cancel said: “If you’re a marketer…and you have not read this book, you’re a poser.”
Maybe that’s a little harsh. However, it stresses the value of this book, that’s all about the psychology of getting people to say yes. In an industry like cybersecurity, where fear-based messaging is falling short, following the principles of persuasion can help you forge an alternative path to content marketing success.
The 7 principles of influence are reciprocity, consistency/commitment, social proof, authority, liking, scarcity, and unity.
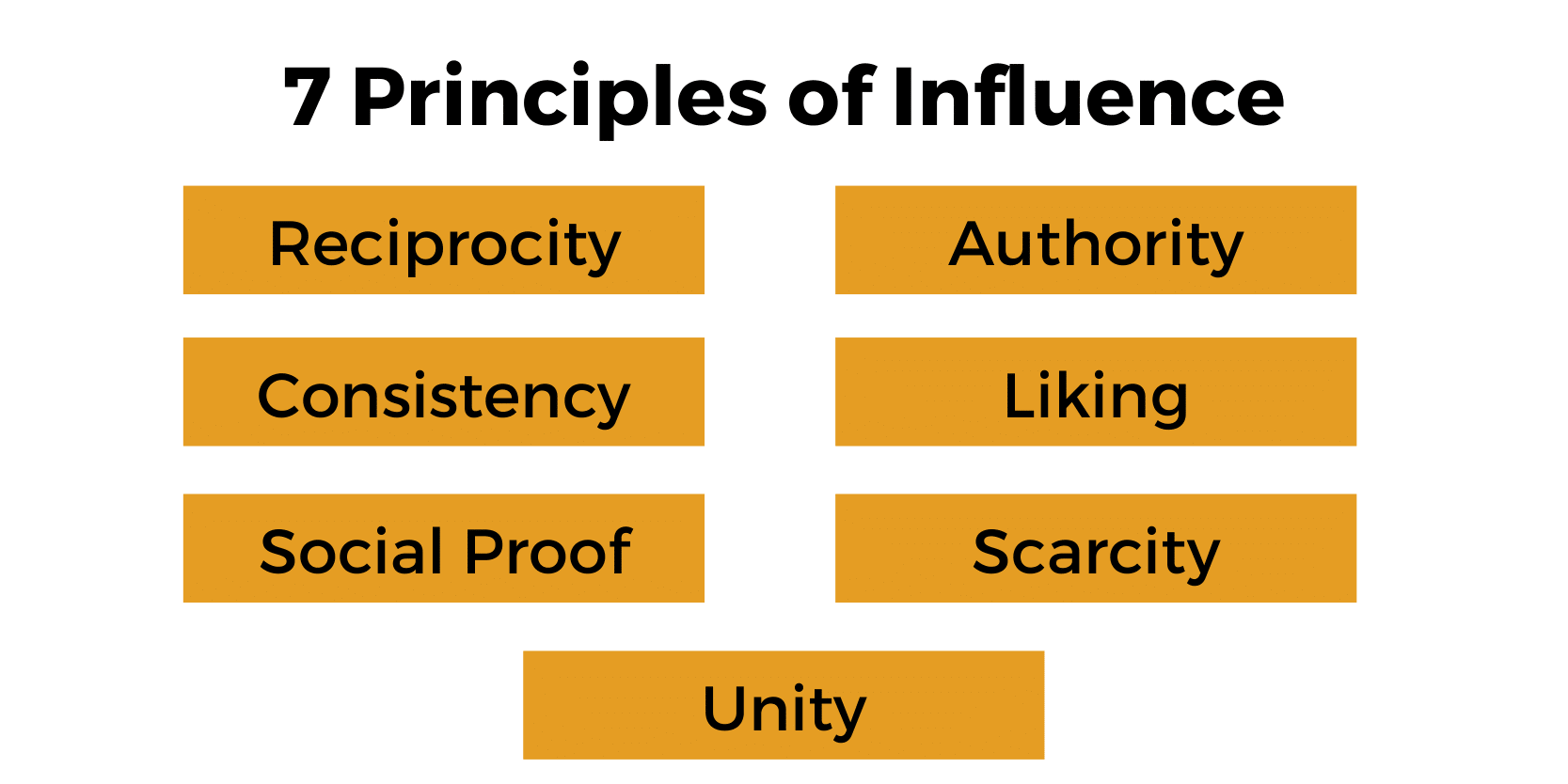
There’s a time and place for each of these principles. But when we’re talking about written content, we can cut the list down to three primary options:
- Reciprocity
- Social Proof
- Authority
Principle #1: Reciprocity
This principle is all about the basic need to return favors. It’s a fundamental desire to take particular actions for those who provide a service first.
Reciprocity is the crux of any inbound or content marketing methodology. It’s the idea that you distribute free content—eBooks, white papers, blog posts, infographics, social posts, newsletters, and everything in between—with the primary focus on providing value to your audience.
Fear-based content doesn’t align with this principle. When FUD is the basis for your content, you’re trying to scare your audience into buying your products. The content is free, but the motivation is to sell instead of providing value first.
Your goal is always to contribute to revenue. Your audience knows that. But shifting to a more positive, customer-centric approach to content better aligns with the principle of reciprocity and will lead to better results.
Principle #2: Social Proof
Another hallmark of marketing in any industry, social proof, is all about catering to a human tendency to prefer products that other people like, recommend, or promote.
This is especially important in the cybersecurity industry. Investing in new cybersecurity solutions is expensive. And any poor investments come with massive costs that just don’t exist with other business systems. Your customers aren’t likely looking to be guinea pigs for unproven solutions.
But you face an uphill battle when trying to create social proof compared to marketers in other industries. Cybersecurity is a somewhat taboo topic. No brand wants to publicize its security incidents (if it can be helped).
At a minimum, you’ll want to add high-profile logos to your homepage. But when it comes to content, you need to be more strategic in your approach. Finding ways to position your customers in a positive light and display quantitative results will be key to generating social proof.
Principle #3: Authority
Love them or hate them, there’s a reason why industry “gurus” is able to continuously build their social followings—they’re seen as authority figures.
It’s human nature to feel more comfortable following the advice of authority figures. Business leaders and security decision-makers don’t want to hear that you’re constantly experimenting with approaches to network security. They want to know that you’re the experts—that they can trust you to secure their businesses.
Enhance your content with quotes from subject matter experts and well-respected leaders. Lean on analyst reports to prove the value of your products.
But be careful. Don’t chase authority by making false claims about your products and services. This can quickly backfire and cause irreparable damage to your brand reputation.
Why You Should Avoid Scarcity as a Persuasion Principle
The glaring omission from this list is the principle of scarcity. It’s might be the most well-known and widely used of Cialdini’s principles of influence.
The scarcity principle says that limited supply increases demand. But within this idea is something that’s often misunderstood in cybersecurity—loss aversion.
Marketers of things like consumer goods and education courses can thrive on loss aversion. Capitalizing on the fear of missing out helps marketers create a sense of urgency. It’s the countdown clock on a heavily discounted product. Or the demand cycle that gets people to camp out for the latest consumer tech product.
When cybersecurity marketers try to embrace the scarcity principle, fear-based messaging becomes prominent. “Don’t wait any longer; upgrade your cybersecurity solutions before the next attack!”
You’d probably be more subtle (and clever) than that. But the point still stands.
It’s difficult to apply loss aversion to cybersecurity because the thing you’re trying to avoid (an attack) is a longer-term issue than something like a consumer goods purchase.
If you can find a way to leverage scarcity in your content marketing effectively, that’s great. Just don’t make it the cornerstone of your content strategy.
Cybersecurity Buyer Personas: Know Your Target Audience
Knowing the right principles of influence to leverage won’t help you much if you aren’t sure who you’re writing content for in the first place.
Before you start writing content as the foundation for your marketing strategy, you need to map out a detailed list of key buyer personas.
But that’s easier said than done.
Because the market is so fragmented, it’s impossible to nail down a one-size-fits-all set of buyer personas that’s 100% accurate for every cybersecurity brand.
Buyer personas for network security solutions may not align exactly with the ones for risk & compliance tools, cloud security, endpoint protection, incident response, MSSPs, and everything in between. And that’s not even to mention the variations that come with different company sizes.
Work with your sales and product marketing teams to get hyper-specific about your ideal customer profiles.
You don’t have to start from scratch, though. By breaking the profiles into enterprise and SMB sets, we can come up with some high-level, generalized cybersecurity personas to get you started.
Enterprise Cybersecurity Buyer Personas
Enterprise deals come with greater revenue potential but also create content marketing challenges as you have to address a larger buying team.
With such large-scale data protection needs and a widespread workforce, enterprise accounts need an intricate hierarchy of stakeholders to address cybersecurity demands.
There are four general personas that you can expect to write content for when targeting enterprise prospects.
Chief Information Security Officer (CISO)
An enterprise-level role that’s dedicated to avoiding data breaches at all costs.
Typically reporting to the Board of Directors and working alongside the CEO, a CISO needs to create clear lines of communication about all-things security.
Pain points include gathering the necessary data to evaluate cybersecurity effectiveness, explaining the importance of activities and investments to non-technical stakeholders, and increasing the budget for new security tools.
While the CISO has significant buying power, your content has to make it easy for them to justify a purchase. That means crafting powerful case studies and leveraging quantitative data bout product benefits.
Chief Information Officer (CIO) and Risk Manager
Outside of the dedicated CISO role, you’ll also have to address those responsible for managing business risk in a more general sense.
Much of the CIO/Risk Manager persona mirrors the CISO profile. They need data that will justify buying decisions, and they’re always looking for more budget money.
These are technical professionals but may not be specifically experienced in cybersecurity. Your data can’t drill too deep into the technical weeds.
Content needs are similar to the CISO. However, making your data points less technical can increase engagement with CIOs.
Risk Analyst
Once you get out of the C-suite level, you’re addressing the technical professionals who devote their time to ongoing intrusion prevention and detection activities.
From a product perspective, cybersecurity specialists need easier ways to generate data for next-level managers. But more than that, they’re focused on managing organizational cybersecurity, making sure human errors can’t take the whole system down.
You have a great opportunity to educate the audience. These technical pros love learning about the latest and greatest advancements in tech. However, if they’re going to propose your brand’s products to higher-level managers, they need to see more than awareness-level blog posts.
The more technical you can get with your content, the better it will perform with these members of the buying team. Show them exactly why your products and services stand above the competition.
Cybersecurity Architect
Another technical pro alongside risk analysts. But the difference is that cybersecurity architects work closely with the CISO. When it comes time to upgrade security solutions, cybersecurity architects are expected to have strong opinions about both the existing tools and potential replacements.
These members of the buying team will want to get hands-on experience with your products and services. Setting up easy ways for them to first see the capabilities of your product will be key.
But before that, cybersecurity architects are generally more willing to experiment with new solutions. They have the technical background necessary to understand the latest innovations and trends. Use content to showcase the deepest technical capabilities of your products and services while also showing that your brand is an authority in a given cybersecurity niche.
SMB Cybersecurity Personas
There’s a certain level of frustration that comes with marketing cybersecurity solutions to SMBs.
You know that content marketing is all about delivering value to your target audience. Cybersecurity should sell itself, though, right? Data breaches and cyber-attacks are pervasive problems that can cost any organization millions of dollars.
But we know now that the fear of data breaches doesn’t always motivate decision-makers to invest more in cybersecurity. That’s especially true for SMBs that don’t have dedicated security pros on staff.
Regardless of persona, effective SMB cybersecurity content marketing is:
- Education First: Take an educational, authoritative approach to explain the specific problems SMBs face when it comes to cybersecurity.
- Maturity-Based: Avoid creating content that’s riddled with industry jargon and acronyms. Your tech is important, but most SMB decision-makers won’t care to go so deep into the details.
- Tailored to Strategic Goals: “Improving cybersecurity” probably isn’t a strategic goal for most SMBs. Figure out what they’re focused on (like executing a digital transformation strategy) and explain how cybersecurity helps in reaching those goals.
- Approachable: If there were a one-size-fits-all cybersecurity solution, the industry wouldn’t be so fragmented. The problem is that SMBs might expect a silver bullet product. Understand the cybersecurity maturity level of your target prospects and create content that is as approachable as possible.
With these key traits in mind, you can effectively create content for the primary SMB cybersecurity buyer personas.
CEO and CFO
The two foremost leaders of an SMB focus on making their organizations as profitable as possible.
While they see the need for IT investments, the relevant data is often too technical for them to completely understand the ROI of that spending. And when profitability is the primary goal, it can be difficult to see cybersecurity as anything other than a cost center.
Educational, awareness-level content can make it clear that cybersecurity is valuable. But CEOs and CFOs are likely more involved in late-stage purchase decisions. If you want them to give the final sign-off, you’ll need case studies that revolve around ROI.
COO (or Another Operations Leader)
Because the highest priority of an operations leader is to keep the business up and running, you can count on cybersecurity to be more of a concern for these decision-makers.
They know that any security incident will derail operations almost entirely. However, they also know that creating a bloated mess of security solutions and processes will hinder operational agility. Operations leaders need to balance productivity with safety.
A COO probably won’t be able to make the final purchase decision for large-scale cybersecurity solutions and services. That means you need to outfit them with the data and talking points necessary to justify a purchase for CEOs and CFOs.
IT Leadership
For many SMBs, in-house IT leadership is dedicated to technical support. Small teams field support tickets and implement policies/processes that limit the effects of human error.
Just because IT leaders are more technical than other SMB leaders, you shouldn’t expect them to be well-versed in cybersecurity. However, when it comes time to implement a new cybersecurity solution, C-level executives will listen closely to the input of IT leadership.
Cybersecurity content for SMB IT leaders isn’t just about education—it’s about giving them the tools and data points needed to educate their non-technical colleagues.
Content Breakdown: 5 Types of Written Content That Help Cybereason Thrive
“Good artists borrow, great artists steal.”—Picasso
The classic Picasso quote is so relevant to the marketing world at large. And in the increasingly crowded cybersecurity industry, following this adage is a necessity.
You don’t have to revolutionize content marketing if you want your cybersecurity brand to stand out. If the written content isn’t working for you, it’s not because your audience isn’t looking for it.
Rather, cybersecurity content marketing falls apart when it’s too reliant on fear-based messaging and fails to address the specific needs of buyer personas.
Turn things around by stealing strategies from the brands that are succeeding with content. One of the best to learn from in recent years has been Cybereason.
In 2019, Forbes named Cybereason in its Next Billion-Dollar Startups list. And while much of that success comes down to product innovation, there’s no denying the role that marketing has played in the growth of their brand in recent years.
Specifically, Cybereason has built out a deep library of written content that serves the educational needs of its enterprise target audience while giving the sales team all the tools it needs to close deals.
Let’s look at 5 key forms of written content that have helped Cybereason strengthen its brand:
- First-Party Research
- Case Studies
- Blog Posts
- Analyst Reports
- Data Sheets
Cybersecurity Content Breakdown: First-Party Research
You need to be seen as an authority in the cybersecurity industry. To do that, you can’t just rely on high-level blog posts that comment on current events.
That’s why Cybereason and other strong cybersecurity brands focus heavily on first-party research.
A strategic advantage you have over content marketers in other industries is that your products and services are actively collecting data about the most pressing challenges your customers face.
The threat landscape is constantly changing, and your products are collecting thousands of data points to help your engineers keep up. Cybereason and others turn that data into first-party research reports on the latest attack vectors.
Look at this research report as an example: Fakespy Masquerades as Postal Services Apps Around the World.
This isn’t just a short overview of what someone like TechCrunch or Dark Reading would release about the threat.
Rather, Cybereason leans on its internal analysts and researchers to uncover as much information about the threat as possible—and explains how they can stop it in its tracks.
There are two key things to notice about this research report.
First, you’ll find that it’s an ungated asset. Cybereason isn’t putting this report out as a lead-gen asset—the way most first-party research is distributed. The ultimate goal is to position Cybereason as an authoritative brand in this industry.
The second thing you’ll notice is that the report goes deep into the technical details of this threat vector.
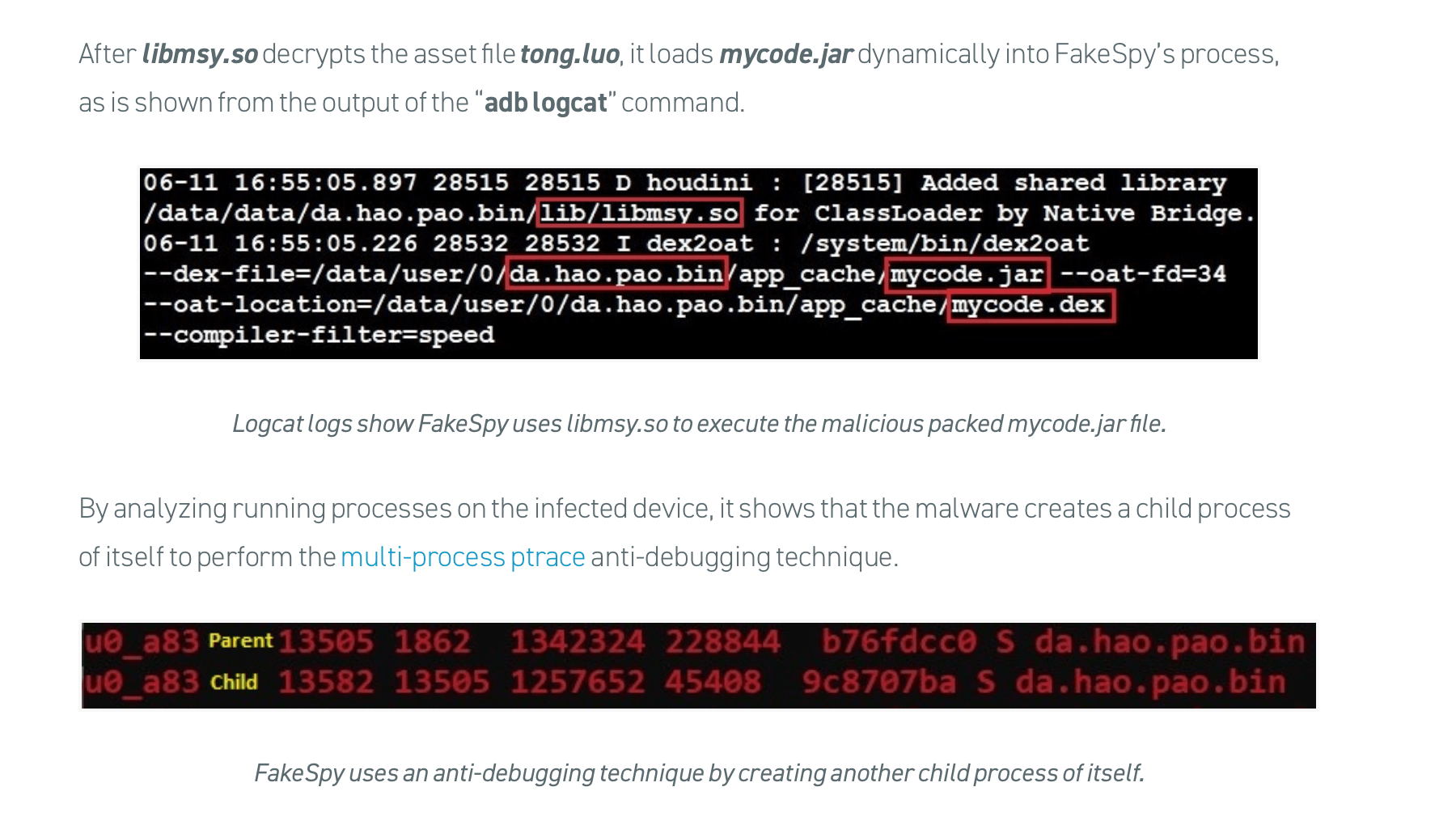
These reports are tailored specifically to the more technical buyer personas that Cybereason has to market and sell to. It’s not about justifying the purchase at the C-level—it’s about showing analysts and architects that Cybereason products are up to the challenge of defending against the most sophisticated threats.
Cybersecurity Content Marketing Breakdown: Case Studies
There’s a fine line between a fluff piece and an impactful case study that highlights the customer while discussing relevant challenges. Cybereason shows how you can talk about cyber threats without succumbing to FUD.
In a case study with Seton Hall University, Cybereason’s primary message isn’t that its products saved the institution from cybersecurity disaster—it’s that they were able to lower costs in the short and long term.
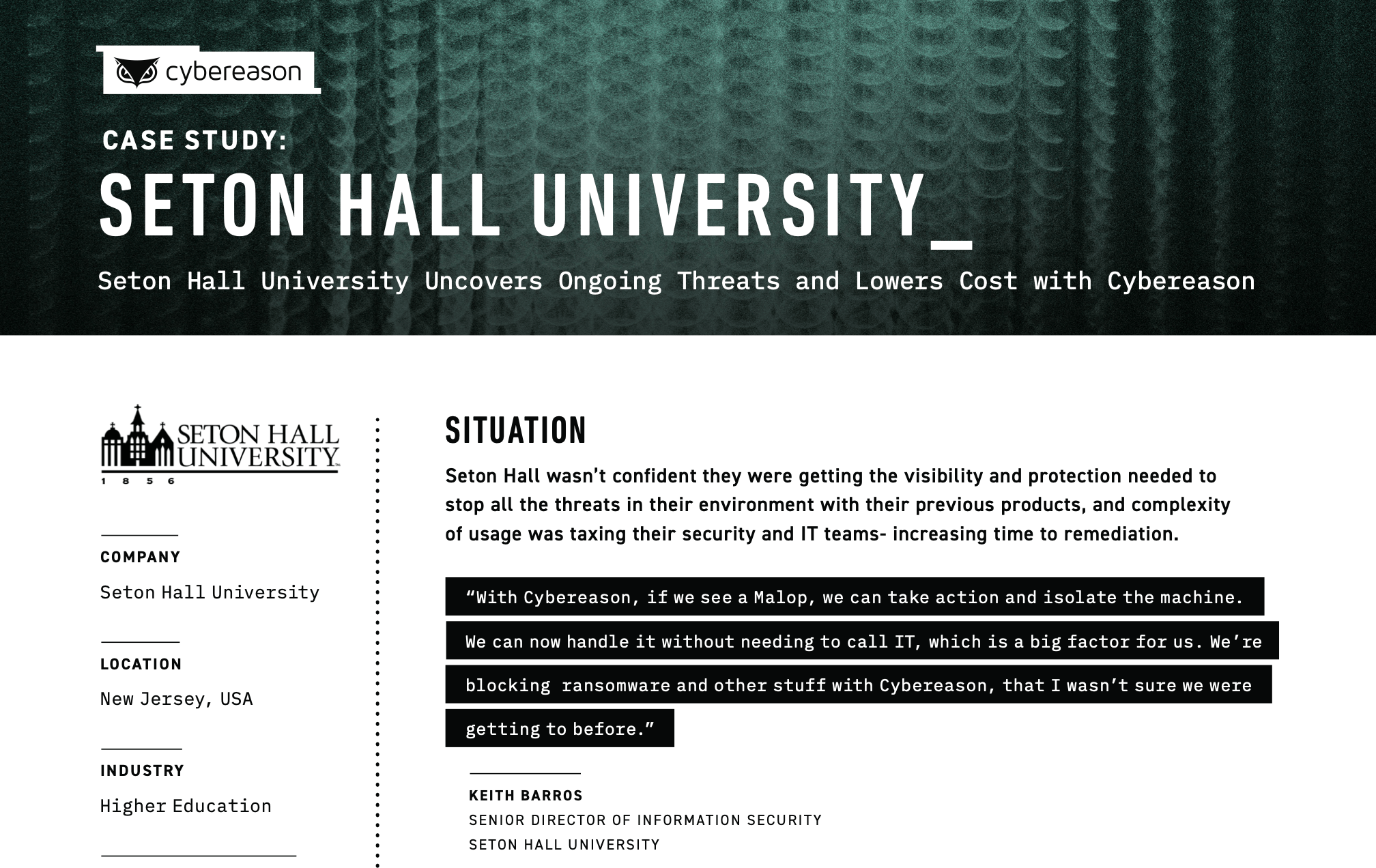
One great takeaway from this case study is that Cybereason isn’t afraid to pick fights with its competitors. This is a highly competitive industry, and it’s important to put a spotlight on any brand differentiator.
Instead of simply explaining how Cybereason helps the university, there are comments about which solutions they replaced and the results.
The combination of quantitative (TCO reductions) and qualitative (quotes about customer service) make this case study an effective tool for persuading C-level decision-makers.
Cybersecurity Content Marketing Breakdown: Blog Posts
Blog posts are essential building blocks of a content marketing strategy. However, it’s easy to get sucked into a “content for content’s sake” cycle with B2B blog posts.
Especially when you’re selling high-consideration cybersecurity products, you can’t exhaust all of your content marketing resources on a high-volume blog publishing schedule.
The analyst reports, first-party research, and case studies are the more valuable pieces for cybersecurity audiences. That’s why Cybereason uses its blog to comment on current events and company news when appropriate.
Most recently, Cybereason has focused its blog posts on the security implications of work-from-home mandates.
Using your in-house team to write massive blog posts for each of your buyer personas won’t leave much time for the bigger (more valuable) projects. Repurpose those bigger pieces of content to fill out the blog and drive downloads of white papers.
Cybersecurity Content Marketing Breakdown: Analyst Reports
If your budget allows it, sponsored analyst reports can increase your authority in the eyes of C-level decision-makers.
Something like this IDC Technology Spotlight can cover both the technical and business benefits of your products.
Because IDC’s VP of Research writes the report, there’s an additional level of trust compared to a white paper written in-house by Cybereason. As much value as this report offers from an educational perspective; it serves as a strong brand-building asset.
The tech spotlight from IDC might be best suited to persuade technical leaders. But when you look at a Total Economic Impact (TEI) study from Forrester, you get the quantitative data necessary to convey value to less technical decision-makers.
Cybersecurity Content Marketing Breakdown: Data Sheets
If you want to reach high-level decision-makers with your content, you have to work around the fact that they’re busy. Worse yet, they’re likely being bombarded with content offerings from all kinds of other cybersecurity brands.
Whether it’s a technical lead looking for quick resources to share with less technical decision-makers or your sales team trying to engage a C-level contact, you need at-a-glance content that can capture attention.
Cybereason solves this challenge with a deep library of data sheets for its various products and services. Look at the MDR data sheet as an example.
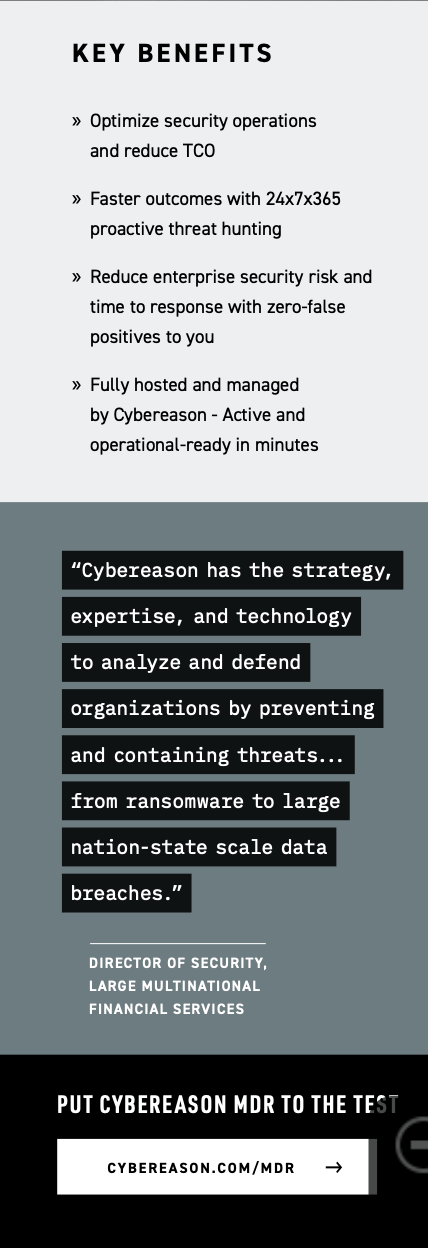
This data sheet and others offer a quick overview of the business benefits that come with Cybereason products and services. While they detail some of the technical product differentiators in the body copy, the data sheets are more focused on quick-hitting overviews.
Creating data sheets for your sales team isn’t a new concept. However, if you’ve been struggling to maximize the value of this content format, following the Cybereason lead can help you refocus.
The High-Volume Cybersecurity Content Marketing Game
When inbound and content marketing first went mainstream, volume was the name of the game.
More content meant more traffic, which meant more leads. And a consistent publishing schedule was key to building trust with your target audience.
Times have changed, though. Now, we know that more content doesn’t automatically equal better results, and content strategies are changing accordingly.
But that might not be true for the cybersecurity industry.
The level of competition combined with the rapid rate of change across the industry makes high-volume content creation almost essential. New threat vectors emerge almost daily. Sophisticated attackers learn how to evade cyber defenses, forcing your engineers to make product changes quickly. And newly funded cybersecurity brands continue to enter the market, trying to overtake your positioning.
The high-volume content game isn’t easy. Companies like Cybereason, which have raised millions of dollars in funding, are able to scale marketing teams quickly and leverage in-house subject matter expertise to fuel content creation needs.
But what if you don’t have that content engine up and running yet? Taking the right approach to content creation is key to keeping pace with competitors with whatever resources you have.
Building Your Writing Team for Effective Cybersecurity Content Marketing
Keeping up with high-content demands forces you to deal with a classic marketing problem—the in-house writer vs. freelancer debate.
Each path has its advantages and disadvantages. With the freelancer route, you get on-demand writing services and access to a wider range of subject matter experts. However, that approach comes at the cost of product expertise and (at times) availability.
When you hire in-house writers, you maximize control over availability and can do more to train for product expertise. However, you lose the flexibility that can help maximize cost efficiency.
Is one approach better than the other?
Not necessarily. Satisfying all of your content demands will take a mix of the two models. The way Jon Bonini, Director of Marketing at Databox, looks at the freelancer vs. in-house writer debate helps make that point.
You need to create a constant stream of content for multiple buyer personas and for every stage of the buyer’s journey. That means you’ll need to strike that balance between on-demand subject matter expertise and adaptable product/service mastery.
The real challenge is sourcing that talent and building out your writing team. Hiring in-house marketers are one thing, but uncovering the right freelancers is a whole different challenge.
That’s where nDash can help. We have a deep network of freelance writers with extensive cybersecurity experience who are fully vetted. And when you’re ready to scale your team, we can help you find the perfect writers for your specific assignments.
Ready to kickstart a winning content strategy for your cybersecurity brand? Forget the fear-based messaging and create all the content necessary to engage your ideal customers.
Reach out and let us help you build your writing team today.